How Attackers Target Siemens Industrial Controllers
See what happens when publicly available penetration testing tools are used against real Siemens S7 controllers — and what it means for your OT environment.
What You’ll Learn
In this on-demand video, you'll explore how attackers use common open-source tools against two of Siemens’ most widely deployed industrial controllers:
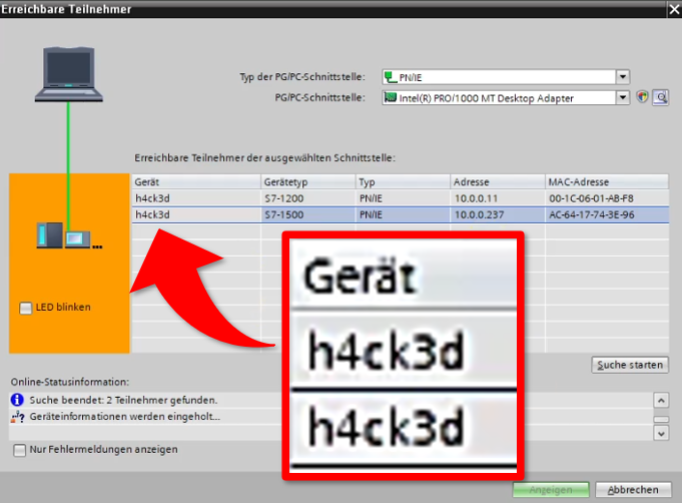
Step 1: Reconnaissance
🔎 Discover industrial devices with tools like Netdiscover, Nmap, NSE, and SNMPcheck
🔎 Learn how a basic scan reveals critical details about device configuration, firmware, and network posture
Step 2: Unauthorized Interaction
⚙️ Use open-source tools to change CPU operating modes remotely
⚙️ Explore the risk of web servers with insecure CPU control functions
⚙️ Understand the impact on process safety and availability
Step 3: Limitations of Tools & the Bigger Picture
🧠 See what open-source tools can’t do — and why misconfigurations still dominate industrial risk
🧠 Get a realistic view of attacker limitations, and how bad setups make things worse
Step 1: Reconnaissance
🔎 Discover industrial devices with tools like Netdiscover, Nmap, NSE, and SNMPcheck
🔎 Learn how a basic scan reveals critical details about device configuration, firmware, and network posture
Step 2: Unauthorized Interaction
⚙️ Use open-source tools to change CPU operating modes remotely
⚙️ Explore the risk of web servers with insecure CPU control functions
⚙️ Understand the impact on process safety and availability
Step 3: Limitations of Tools & the Bigger Picture
🧠 See what open-source tools can’t do — and why misconfigurations still dominate industrial risk
🧠 Get a realistic view of attacker limitations, and how bad setups make things worse
Why This Matters
Attackers don’t need zero-days.
They need access, misconfigurations, and unprotected devices.
By understanding how common tools interact with your PLCs, you become a better defender — and a more valuable OT security professional.
🔒 Get Instant Access (Free)
Enter your email to unlock the full video
No slides. Just real tools, real PLCs, and real tactics.
Bonus:
You’ll also get access to the OT Attack Surface Checklist
30 practical controls to secure your environment.
You’ll also get access to the OT Attack Surface Checklist
30 practical controls to secure your environment.
By submitting the form you agree to our Terms & Conditions and Privacy Policy.